The Definitive Guide to Preventing Insider Threats in Small and Midsize Businesses
.png)

What is an Insider Threat?
An Insider threat happens when someone within your organization (an employee, contractor, vendor, or consultant), misuses their access to cause harm. Sometimes it's intentional, like stealing data or sabotaging systems. Other times, it's accidental, like an employee clicking a phishing link or sharing credentials.
Either way, insider threats are one of the most costly and difficult to detect cybersecurity challenges today.

Why Every Organization is Vulnerable
If your company has employees or third-party vendors, you're already at risk. As your business grows, so does your exposure. More people means more access points—and more opportunities for mistakes or malicious intent.
What's the good news? Most insider threat incidents can be prevented with proactive security measures and awareness.
Drawing on our extensive experience with insider threats, this guide provides refined countermeasures to address these threats effectively.

The First Line of Defense: Background Checks
The best defense against insider threats begins before someone even steps through the door.
When posting job openings, it's easy to overlook how much information you're sharing publicly. But cybercriminals often use open job data to learn about your company's tools, systems, and workflows. That information can then be exploited to craft targeted phishing campaigns or even prepare for internal attacks.
Here's what that might look like in practice:
What Not to Post in job Listings
"We are searching for someone with expertise using PostgreSQL, MongoDB, and Python scripting for batch jobs that run every evening at 5pm."
Why it's risky: This post reveals your tech stack (PostgreSQL, MongoDB, Python) and operational timing (batch jobs at 5pm). That's valuable intelligence for attackers who could time their actions or exploit known vulnerabilities.
What To Post for Job Listings:
"We are searching for someone with expertise building and maintaining popular databases and large data sets with automation."
Why it's safer: This post still attracts qualified candidates but avoids disclosing internal systems or schedules. It protects your infrastructure details while communicating the core skills you're seeking.
When creating job listings, always ask:
- Does this reveal what systems we use internally?
- Could someone use this information to target our organization?
- Are we sharing just enough to attract the right candidates without oversharing operational details?
Being intentional about what you disclose is your first line of defense. It sets the tone for security-aware culture from day one.
And when it comes to screening candidates, go beyond the basics. Outsource to recruiters who perform comprehensive background checks and first rounds of interviews, including federal-level verification when possible.
The One-Week Employee: Frank's Story
Let's rewind to a real situation that changed the way hiring was handled forever.
Frank was hired for a role in a national critical infrastructure organization. His background check (just $75) came back clear. Five days later, he was escorted out of the building, access revoked.
What went wrong?
The background check, labeled "National Criminal Background Check," only covered locations Frank listed as previous residencies. It didn't search federal databases or non-digitized records.
Turns out, Frank had been convicted of a federal crime and was on probation (which he did not disclose). But since the check didn't include federal data, the record never appeared.

What Went Wrong and How We Fixed It
Our company realized that while fingerprinting was required, it was done after hiring. We didn't want to pay for it unless the candidate accepted the job. That delay created a window of vulnerability.
When we switched to pre-employment fingerprinting and worked directly with the FBI, everything changed.
Fingerprints allowed us to detect identity theft, false Social Security numbers, and prior federal arrests.
FBI's Identity History Summary Checks
We also implemented:
- Federal, state, and local checks for every candidate
- Continuous monitoring of employees in sensitive roles
- Law enforcement alert services that notify HR of employee arrests or convictions
- Regular credit checks for employees with access to financial data or networks
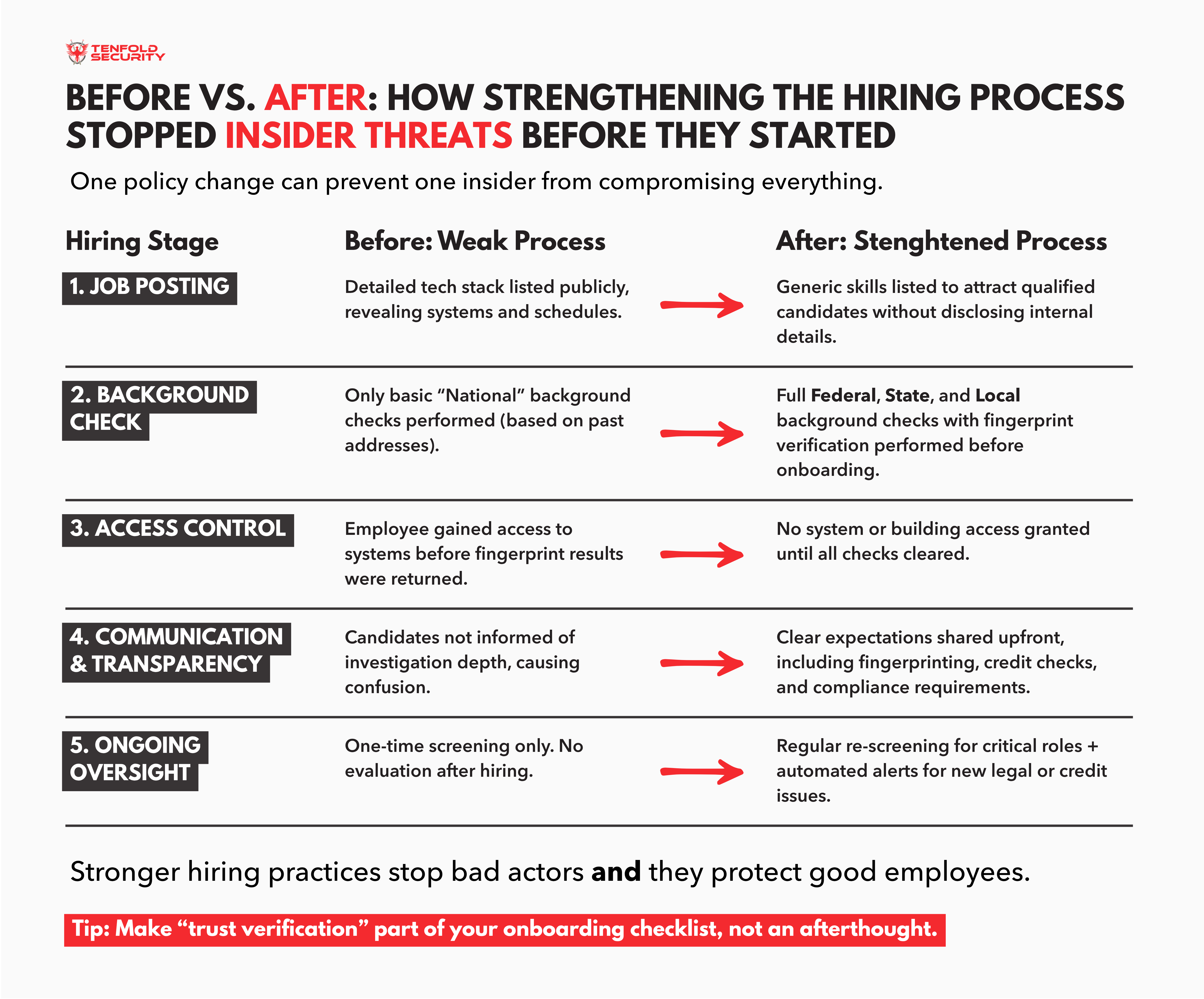
Lessons Learned: Building a Strong Defense
- Perform fingerprinting before onboarding. It's worth the cost.
- Communicate transparency. Let employees know checks are routine, not punitive.
- Monitor long-term employees, too. Risks don't stop at hiring.
- Use law enforcement alert integrations. They offer proactive awareness.
- Reassess compliance requirements regularly. Don't assume "good enough" meets today's threats.

Key Takeaways for Your Organization
- Insider threats often come from trusted individuals, not outsiders.
- Comprehensive background checks are a business safeguard, not just a compliance checkbox.
- Continuous monitoring builds trust and resilience.
- Even small businesses can adopt scalable insider threat prevention measures.
Final Thoughts
The story of Frank serves as a reminder: one unchecked hire can unravel years of progress.
By strengthening your hiring process and maintaining continuous vigilance, you can prevent insider threats before they happen.
Remember: your first line of defense starts with who you let in.
FAQs
- Unusual data access or downloads outside normal work hours
- Employee bypassing security controls
- Increased use of removable drives or file-sharing tools
- Sudden changes in job satisfaction, financial distress, or communication patterns
For small businesses, even a single insider incident can be devastating, often leading to permanent closure within six months.
Preventative measures like background checks, access control, and employee monitoring cost a fraction of that and can save your organization from long-term financial and brand damage.
- Identify critical assets and data
- Define insider threat indicators and escalation
- Implement layered background checks
- Train all staff on data handling and reporting suspicious activity
- Continuously evaluate and adjust based on incidents
- Require MFA
- Use VPNs and endpoint protection
- Limit access to only what’s necessary for each role
- Educate employees on phishing and data handling
- User Behavior Analytics (UBA/UEBA) to detect unusual patterns of activity
- Data Loss Prevention (DLP) to stop sensitive data from leaving your systems
- Security Information and Event Management (SIEM) to centralize and correlate logs
- Endpoint Detection and Response (EDR) to track and mitigate threats at the device level
- Relying solely on basic national background checks
- Skipping federal or fingerprint-based checks to save cost
- Not verifying previous employment or references
- Conducting checks only once (at hire) and never again
- Ignoring behavioral red flags due to urgency in hiring
- Regular awareness training
- Clear reporting channels for suspicious activity
- Recognition for responsible security behavior
- Leadership that models good practices
ready to elevate your cybersecurity strategy?

Stay ahead of threats with Tenfold Security. Don't miss our upcoming resource: The Ultimate Guide to Cybersecurity for SMBs.
This comprehensive guide will equip you with everything you need to protect your business from cyber threats.
Sign up now to be notified the moment it's available and gain exclusive early access.


