5 Hidden Software Inventory Risks: How Users Bypass Admin Privileges & What You Can Do


Table of contents
Introduction: Why Software Inventory Isn't Enough
5 Ways Users Bypass Admin Privileges
- Portable Applications
- Browser Extensions & Plugins
- Scripting Languages
- Web-Based Tools
- Third-Party App Installers
Real-World Risks and Case Study
Introduction: Why Software Inventory Isn't Enough
You’ve done the work: created a clean software inventory, locked down devices, and implemented an approved software list. But users always find workarounds—especially in environments where only admins can install software. This article uncovers the top five ways users bypass security restrictions and how you can defend against them.

5 Ways Users Bypass Admin Privileges
1. Portable Applications
These are apps designed to run without being formally installed—think USB or user directory execution.
Examples: Portable Chrome, VS Code Portable, file-sharing apps.
Risk: These apps often bypass endpoint security and leave no audit trail.
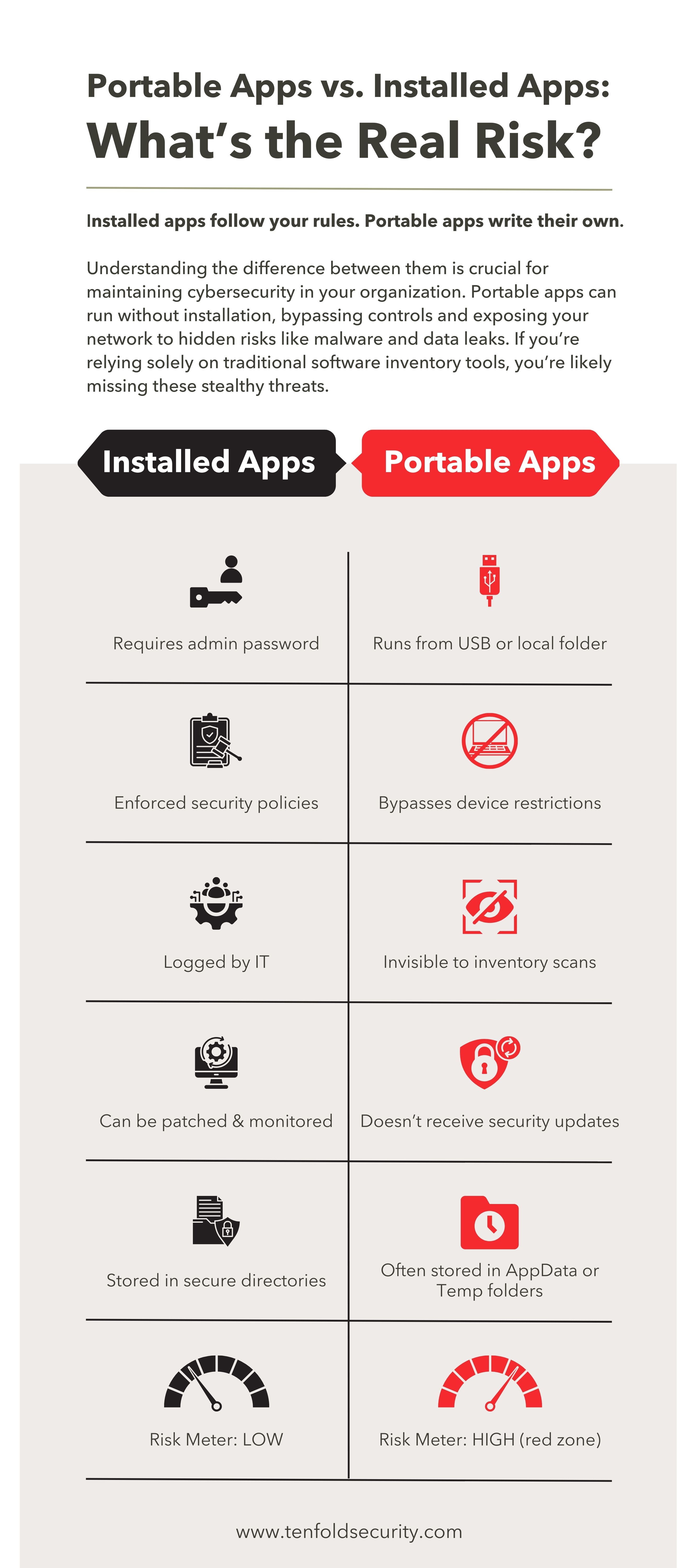
2. Browser Extensions & Email Plugins
Browsers often let standard users install third-party extensions, some of which are malicious.
Real Example: A developer installed a sport-streaming extension that turned their system into a TOR exit node, exposing the network to the dark web.
Risk: Extensions can execute remote code, access passwords, or act as data leaks.
3. Scripting Languages (Python, PowerShell, etc.)
Users may run scripts using built-in interpreters to download payloads or modify system settings.
Risk: These can lead to remote code execution and privilege escalation.
4. Web-Based Tools
Cloud IDEs, online converters, and browser apps bypass the need for installations.
Risk: These platforms can be used to upload sensitive data outside of controlled environments.
5. Third-Party Installers (e.g. Chocolatey, Ninite)
These tools offer package managers that install software with pre-configured privileges.
Risk: In secure environments, this is essentially side-loading software without approval.

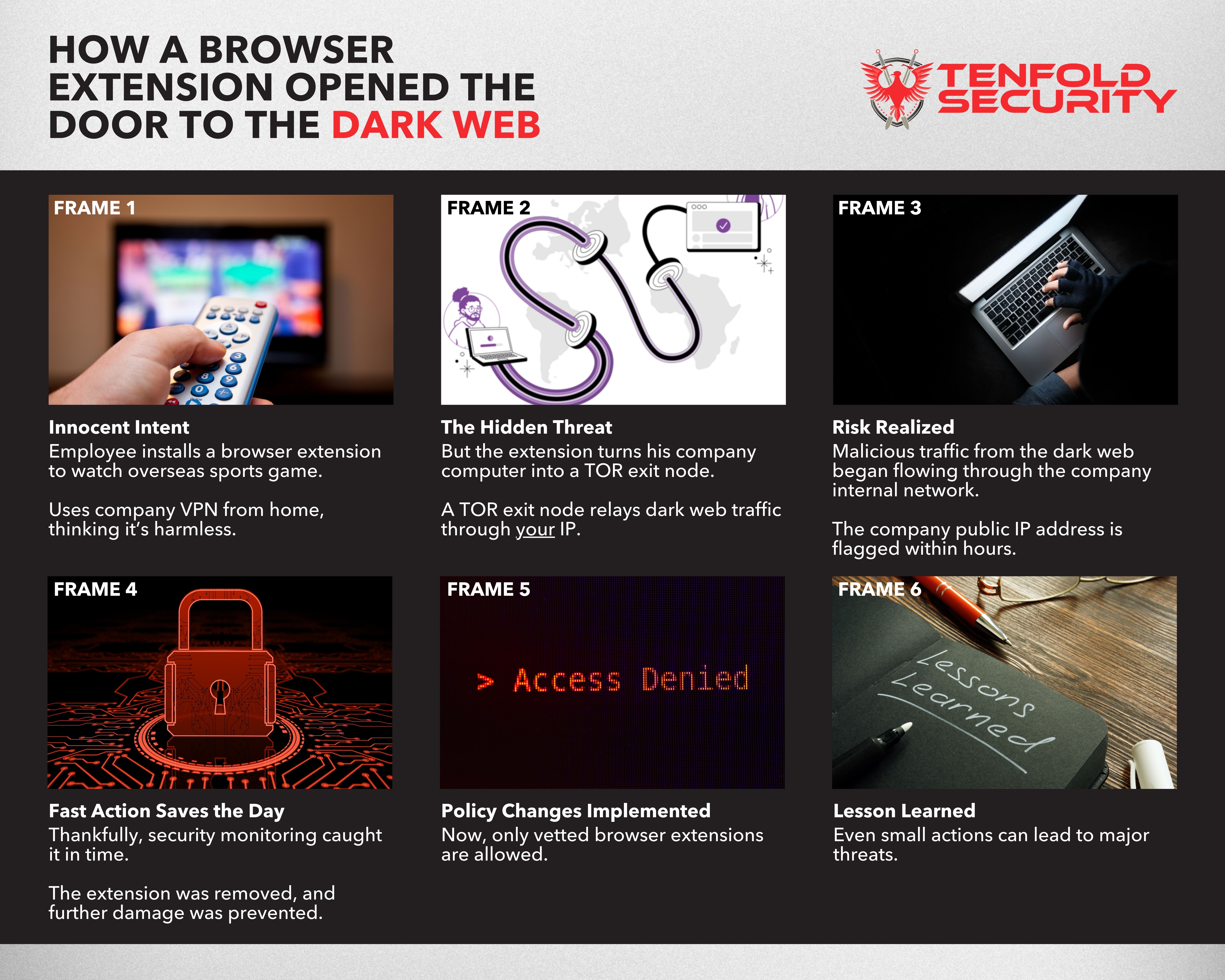
Real-World Example: When a Browser Extension Becomes a Backdoor
Not long ago, a New York-based employee for a former company installed a browser extension to get around geolocation restrictions so he could stream a live cricket match being broadcast overseas. He was working from home and connected to the corporate network through the company VPN. Seemingly harmless, right?
Unfortunately, the extension did more than unlock sports content. It turned his desktop into a TOR exit node—a relay point for internet traffic coming from the TOR (The Onion Router) network, which is often used for anonymous browsing and can include dark web traffic.
What's a TOR Exit Node?
A TOR exit node is the final point in the TOR network where encrypted traffic becomes readable and hits the regular internet. If your company becomes one, it routes potentially illegal or malicious activity through your device, making your IP address the public face for that traffic.
In this case, that meant dark web users were unknowingly accessing the internet through our internal network.
Within hours, our public IP address was flagged on multiple threat intelligence feeds as suspicious. Thankfully, our monitoring tools caught it early. The threat was isolated, the extension was removed, and we avoided any significant damage.
As a result, we implemented strict controls on browser extensions—blocking installations that haven’t been vetted and approved by our security team.
Lesson learned: Browser extensions seem small, but they can create big vulnerabilities. Always monitor, manage, and educate your users.
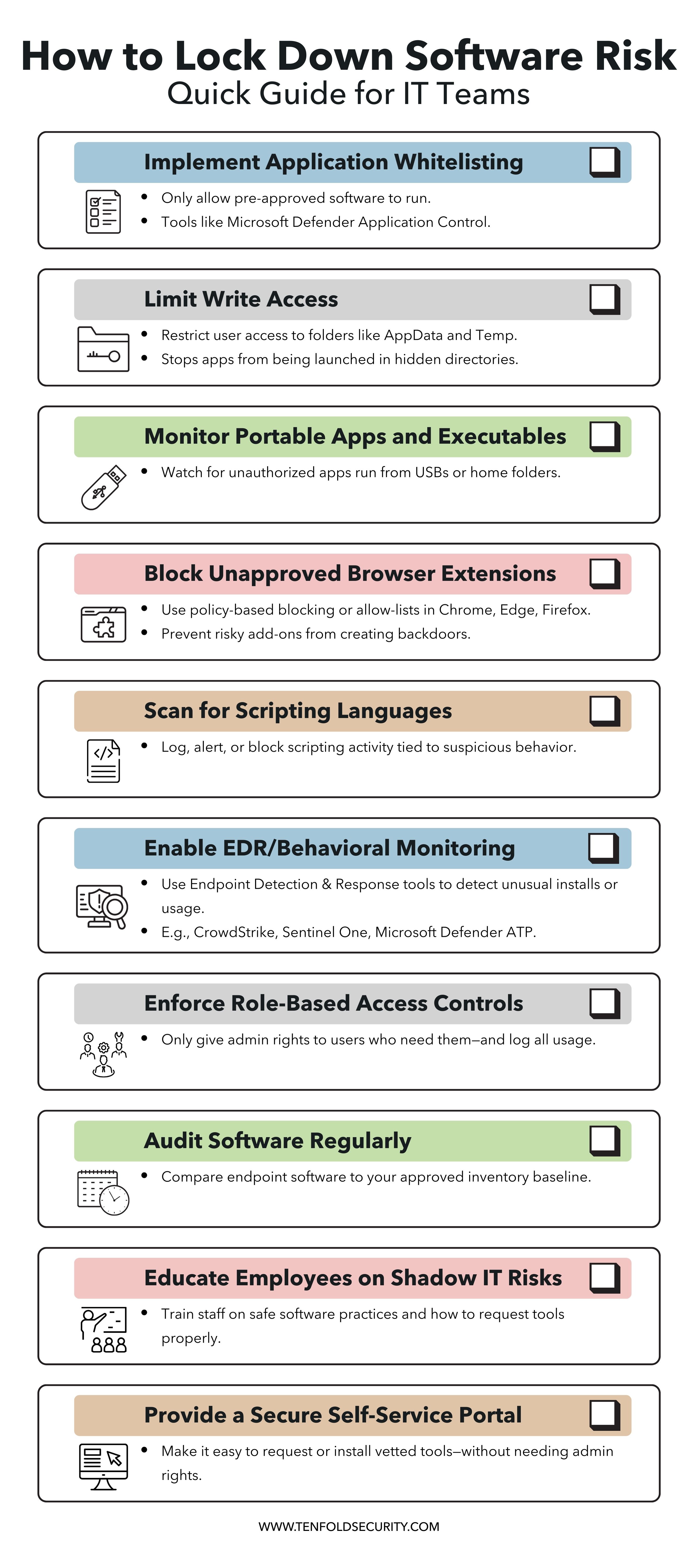
How to Secure Your Software Inventory
1. Use Application Whitelisting
Tools like Microsoft Defender Application Control (MDAC) or AppLocker block non-approved software, restricting what can be executed.
2. Restrict User Write Access
Limit write permissions to critical directories to reduce abuse of user-writable paths.
3. Monitor Executables in Unusual Locations
Configure alerts for running from unusual locations like AppData, Temp, or external drives like USBs.
4. Use Endpoint Detection and Response
EDR tools like CrowdStrike Falcon can detect suspicious behaviors such as privilege escalation attempts or unauthorized software executions.
5. Audit Regularly
Set a monthly or quarterly cadence to review software baselines and deviations from the approved software lists.
6. Educate End Users
Train users on the risks of unauthorized installations and how to request software the secure way.
7. Offer a Self-Service
Give users a fast, secure way to request and install pre-approved tools and extensions without needing admin rights.
Conclusion
Firewalls, antivirus, and endpoint tools are all critical—but software inventory management often gets overlooked. By understanding how users work around restrictions, you can tighten controls, prevent data loss, and maintain security without slowing productivity.
ready to elevate your cybersecurity strategy?

Stay ahead of threats with Tenfold Security. Don't miss our upcoming resource: The Ultimate Guide to Cybersecurity for SMBs.
This comprehensive guide will equip you with everything you need to protect your business from cyber threats.
Sign up now to be notified the moment it's available and gain exclusive early access.


