How Attribution Stopped a Rogue Employee from Stealing Sensitive Financial Data


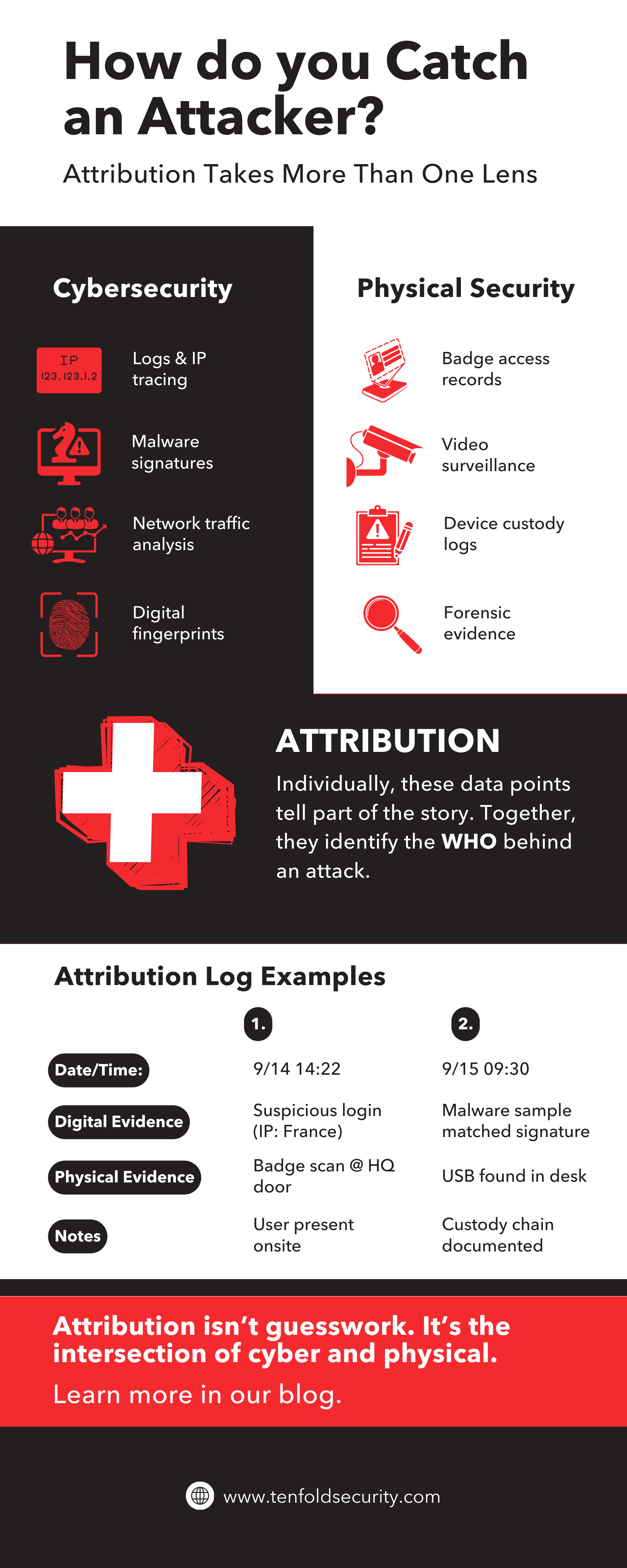
Introduction: What is Attribution?
When a data loss incident happens, the first question isn’t just what happened. It’s who did it, how they did it, and why. This process is called attribution, and without it, organizations can’t respond effectively or prevent future attacks.
And sometimes, attribution isn’t found in the firewall logs or intrusion detection systems. It’s hiding in the hallways, the printers, and even the dumpsters. We’ve seen firsthand how attribution (using both cybersecurity and physical security) can stop insider threats in their tracks.
Here’s a true story of how one underperforming employee nearly walked out with sensitive financial data for months…until attribution brought the truth to light.
A Routine Investigation Turns Strange
It started with a finance employee who was flagged for poor performance. Before his termination, we reviewed his access logs as a precaution.
On paper, nothing looked suspicious. He copied files to his desktop, deleted them hours later, and moved on with his day. It could have been routine.
But something didn’t feel right.
When we check his physical access logs, the pattern jumped out:
- He arrived at normal times
- He left at exactly the same time every day
Most people vary—a quick chat with a coworker, a restroom stop, a late meeting. But this employee’s exits were clockwork precise. Too precise.

Lesson 1: Implement Anti-Passback
This is where anti-passback systems matter. If you require employees to badge both in and out, you’ll spot irregularities sooner. This was the only way we could track both the employee’s arrival and departure.

Following the Trail
Video footage confirmed our suspicions. Every afternoon at 3:50 p.m., he packed his belongings, left the sixth floor, and disappeared. When he didn't appear on the first floor, a quick search found that he exited the elevator on the third floor.
There, he quietly retrieved a coworker’s badge from a desk. With his colleague’s badge in hand, he returned to the elevator, badged himself out of the building under his own credentials…and then went back upstairs to the sixth floor using the stolen badge.
What happened next was almost unbelievable.
At his desk, he collected a small trash bag that appeared to weigh almost nothing. With the trash bag in hand, he returned to the third floor and returned his coworker's badge to his desk. He then went to the first floor but exited through the service side of the elevator onto the loading dock.
He carried his trash bag down to the loading dock, tossed it into the dumpster, and moments later slipped out through the dock stairs. Dock workers greeted him as he walked past, none the wiser.
When he thought the coast was clear, he retrieved the bag from the dumpster and left the building with sensitive documents in hand.
This happened every two weeks, right before payday.
Lesson 2: Lock Badges or Require Employees to Take Them Home
We discovered that employees did not have to use badges to get into the building at the turnstiles. They could use their fingerprints to enter and badges to leave the building which circumvented our multi-factor entrance requirement.
Many people simply tailgated another employee to leave the office and these security holes were common knowledge all the way to the CEO.
This exposed two weak points: badge security (employees leaving badges at desks) and physical exit loopholes (loading docks were not monitored like front entrances and a multi-factor entrance work around).
Both weak points gave him the cover he needed.

Setting the Trap
We set up a small operation with the dock workers. The next time he tossed his bag, one worker retrieved it while another stalled him with conversation.
When he couldn’t find the bag, panic set in. He searched the dumpster for ten minutes before storming off.
The next morning, he fired off angry emails demanding to know where “his” trash bag had gone—claiming he had thrown away his wedding ring by accident.
Video evidence told a different story.
Inside the bag? Confidential financial documents and private data.
Printing the Evidence
The final piece of evidence came from printer logs. Our secure printing system tied every printed page back to a user. He had been downloading financial records, printing them, and deleting them from his workstation.
Between access logs, video surveillance, printer records, and eyewitness accounts, we had the attribution we needed. He was terminated and law enforcement recovered the documents from his home.
Without attribution, his activities might have continued for months unchecked.
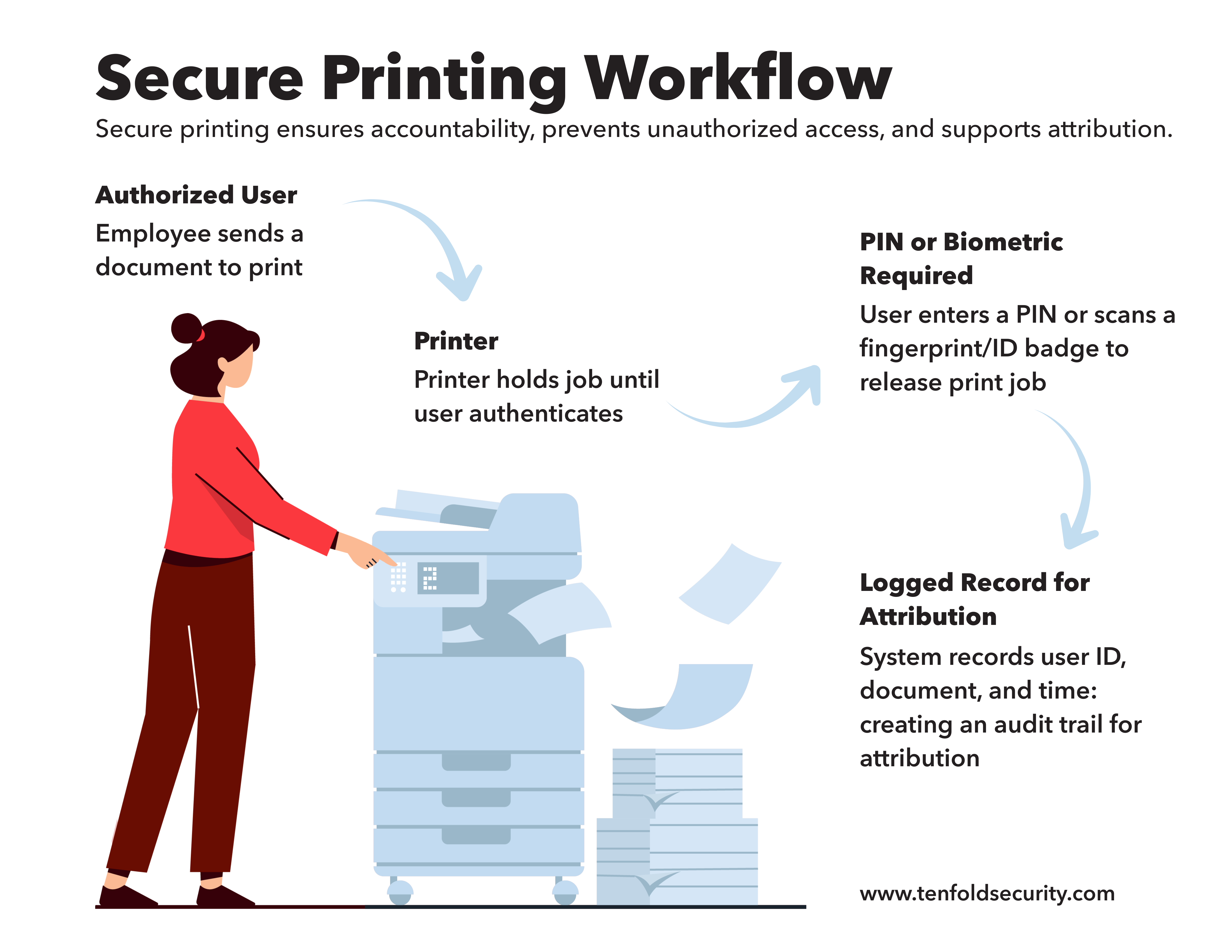
Lesson 3: Implement Secure Printing
Secure printing policies—PINs, biometrics, and logging—make sure you can track exactly who printed what. Without them, attribution would have been impossible.
Why Attribution Mattered
Without attribution, this employee could have continued his scheme for months unchecked. Technical logs alone didn’t reveal the problem. It was the combination of physical security, monitoring, and process enforcement that painted the full picture.
Lessons Learned
Here’s what you can take away from this case:
- Implement Anti-Passback: Require employees to badge in and out for accurate activity tracking.
- Enforce Badge Security: Don’t allow badges to be left behind; pair with biometrics when possible.
- Use Secure Printing: Require PINs or biometrics to release print jobs and keep detailed logs.
- Strengthen Physical Access: Loading docks and vendor areas must be secured, not overlooked.
- Audit Logs Regularly: Technical data is useless without consistent review and correlation.
- Educate Employees: Train staff to understand that physical security is just as critical as cybersecurity.
Attribution isn’t optional. It’s the difference between “we think something happened” and “we know exactly who, how, and when.”

ready to elevate your cybersecurity strategy?

Stay ahead of threats with Tenfold Security. Don't miss our upcoming resource: The Ultimate Guide to Cybersecurity for SMBs.
This comprehensive guide will equip you with everything you need to protect your business from cyber threats.
Sign up now to be notified the moment it's available and gain exclusive early access.


